EDR solutions continuously monitor endpoint activities in real-time, looking for abnormal patterns or behaviours that may indicate a security threat.
Endpoint Detection and Response

There is no escaping the fact that cybercrime has risen exponentially in recent years, and this trend is set to continue. Threat actors are becoming increasingly sophisticated as to how they access your network, and once in, they laterally move through it, encrypting your data, but not until they have stolen it first. Sadly, the cybersecurity landscape has shifted, and the prospect of a business sustaining an attack has moved from being an ‘if’ to a ‘when’ for many organisations. Recent statistics show that hackers are in organisation systems for an average of 276 days before the main attack. During this time, they use exploits and tools to progress through the system to discover the configuration and setup of your server and endpoint estate, including backups. They will gather credentials, files and locations and steal company data.
Traditional antivirus methods are no longer enough to detect the most sophisticated threats; this is because they focus on ‘known’ threats, whereas the latest threats are ‘unseen’. EDR is a critical component of cybersecurity strategies to detect, respond to, and mitigate cyber threats. EDR systems are designed to monitor and analyse activities on endpoints, such as computers, servers, and mobile devices, to identify and respond to suspicious or malicious behaviour.
Ransomware attacks are malicious activities conducted by cybercriminals or ransomware groups with the aim of exfiltrating sensitive data in the form of customer data, trade secrets and other confidential information with the sole purpose of causing maximum destruction. Many businesses think its enough to simply restore their data from backups and avoid paying the ransom, however the cybercriminals have already encrypted the data, and non-payment of the ransom could see it resold on the dark web, so payment is therefore non-negotiable. The level of sophistication and style of attack are forever changing.
What is Endpoint Detection and Response (EDR)?
Endpoint Detection and Response (EDR) is a cybersecurity solution designed to identify and respond to advanced threats on individual devices or endpoints.
![]() Detection: EDR solutions continuously monitor and collect data from endpoints to identify abnormal or suspicious behaviour. This can include activities such as unusual file access patterns, unauthorized system changes, or abnormal network traffic.
Detection: EDR solutions continuously monitor and collect data from endpoints to identify abnormal or suspicious behaviour. This can include activities such as unusual file access patterns, unauthorized system changes, or abnormal network traffic.
![]() Response: Once a potential threat is detected, EDR tools provide a set of response actions to contain, investigate, and mitigate the impact of the threat. Responses may include isolating the affected endpoint from the network, quarantining malicious files, or initiating further investigation.
Response: Once a potential threat is detected, EDR tools provide a set of response actions to contain, investigate, and mitigate the impact of the threat. Responses may include isolating the affected endpoint from the network, quarantining malicious files, or initiating further investigation.
![]() Forensics: EDR solutions often include forensic capabilities, allowing security teams to analyze the details of an incident after it has occurred. This helps understand the attack vector, identify vulnerabilities, and implement measures to prevent future incidents.
Forensics: EDR solutions often include forensic capabilities, allowing security teams to analyze the details of an incident after it has occurred. This helps understand the attack vector, identify vulnerabilities, and implement measures to prevent future incidents.
![]() Real-time Monitoring: EDR solutions provide real-time monitoring of endpoint activities, allowing security teams to respond quickly to emerging threats. This is crucial for minimizing the dwell time of attackers on a network.
Real-time Monitoring: EDR solutions provide real-time monitoring of endpoint activities, allowing security teams to respond quickly to emerging threats. This is crucial for minimizing the dwell time of attackers on a network.
In summary, Endpoint Detection and Response is a crucial component of modern cybersecurity strategies, allowing organisations to detect and respond to advanced threats targeting individual devices within their network. It plays a vital role in enhancing overall security posture by reducing the impact of security incidents and preventing the spread of threats across the network.
What is Lateral Movement?

Lateral movement refers to the techniques that a cyber attacker uses, after gaining initial access, to move deeper into a network in search of sensitive data and other high-value assets. After entering the network, the attacker maintains ongoing access by moving through the compromised environment and obtaining increased privileges using various tools.
It allows a threat actor to avoid detection and retain access, even if discovered on the machine that was first infected. And with a protracted dwell time, data theft might not occur until weeks or even months after the original breach.
After gaining initial access to an endpoint, such as through a phishing attack or malware infection, the attacker impersonates a legitimate user and moves through multiple systems in the network until the end goal is reached. Attaining that objective involves gathering information about multiple systems and accounts, obtaining credentials, escalating privileges, and ultimately gaining access to the identified payload.
Modern security and response for your estate.
Here are key reasons why EDR is vital for fighting cybercrime:
Advanced Threat Protection: Traditional antivirus solutions are effective against known threats but may struggle with newer, more sophisticated attacks. EDR goes beyond signature-based detection, employing advanced techniques such as behavioural analysis, machine learning, and heuristics to identify previously unseen threats and zero-day vulnerabilities.
Incident Response and Investigation: EDR provides detailed insights into security incidents, offering information on the nature of the threat, the extent of the compromise, and the tactics employed by attackers. This data is invaluable for cybersecurity teams during incident response and forensic investigations, helping them understand the attack lifecycle and improve overall security posture.
Behavioural Analytics: EDR systems use behavioural analytics to establish a baseline of normal behaviour for each endpoint. Deviations from this baseline are flagged as potentially malicious, enabling the detection of anomalous activities that may indicate a security incident. This proactive approach helps organisations identify threats before they can cause significant harm.
Compliance Requirements: Many industries and regulatory frameworks require organisations to implement measures for continuous monitoring, threat detection, and incident response. EDR helps organisations meet these compliance requirements by providing the necessary tools and capabilities to protect sensitive data and maintain a secure computing environment.
Adaptability to Evolving Threats: The cybersecurity landscape is dynamic, with attackers constantly evolving their tactics. EDR solutions are designed to adapt to new and emerging threats, making them a crucial component of a proactive and resilient cybersecurity strategy.
In summary, EDR plays a vital role in the modern cybersecurity arsenal by providing real-time threat detection, advanced protection against evolving threats, and robust incident response capabilities. Its ability to offer endpoint visibility and control, coupled with behavioural analytics, makes EDR an essential tool for organisations looking to defend against the ever-growing sophistication of cybercrime.
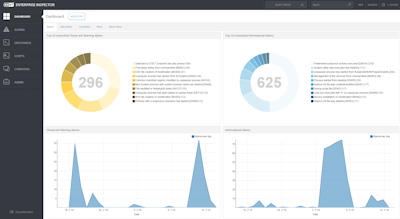
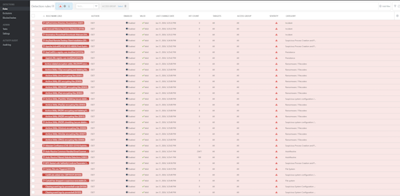
What can EDR recognise?
EDR gathers logs from multiple sources to form a picture of what is going on. This can be what software is being run for remote activities, such as remoting to another machine or remotely executing software file access, creation or renaming, credential stealing, etc. Based on users' activities, this helps build a picture of whether these activities are malicious or everyday use. The key activities EDR will recognise:
Malware and Ransomware: EDR solutions can detect the presence of malicious software, including traditional viruses, worms, Trojans, and ransomware. They identify unusual file behaviour, unauthorized access, or suspicious patterns indicating malware infection.
Fileless Attacks: EDR tools can detect fileless attacks where malware operates in memory without leaving traditional file traces. These attacks often leverage scripting languages or exploit vulnerabilities in legitimate system processes.
Phishing and Credential Theft: EDR can detect phishing attempts and instances of credential theft. It monitors for suspicious login activities, unauthorized access attempts, and anomalous user behaviour that may indicate compromised credentials.
Exploits and Vulnerability Exploitation: EDR solutions can identify attempts to exploit vulnerabilities in operating systems, applications, or software running on endpoints. They monitor for unusual system changes, privilege escalations, or attempts to exploit known weaknesses.
Data Exfiltration: EDR tools can detect unauthorized attempts to transfer sensitive data from the network. This includes monitoring for unusual network traffic patterns or the copying of large amounts of data.
Command and Control (C2) Communications: EDR solutions look for signs of communication between compromised endpoints and external command and control servers. Unusual network traffic or communication patterns can indicate a compromised system trying to establish contact with malicious entities.
Insider Threats: EDR can help identify suspicious activities within the organization, such as employees or contractors engaging in unauthorized access or data exfiltration.
Zero-Day Attacks: While not foolproof, EDR solutions can detect certain zero-day attacks by identifying abnormal behaviour or patterns that deviate from the baseline of normal activities on endpoints.
Advanced Persistent Threats (APTs): EDR effectively detects and responds to sophisticated and long-term cyber threats that often involve multiple stages of attack, making them harder to detect with traditional security measures.
What does Blue Sky Systems offer for EDR?
Blue Sky Systems have teamed up with ESET to offer anti-virus, deeper endpoint firewalling, host-based intrusion detection and EDR.
We can offer this as a monthly fee instead of annually to help with cash flow, along with installation support and 24/7 Security Operations Centre (SOC). The charging model is per endpoint or Operating System (OS) that you wish to protect and whether you wish for external SOC or you wish to keep it in-house.
The system has the ability to kill processes and isolate machines, among other automatic remediation options, in certain high-priority detections. Automated responses are generally not desired for those deemed lower priority as this could affect Business-As-Usual (BAU) work. In those situations, either SOC can review these, or you can be emailed to review them yourself.
We can tailor the solution and our SOC services to provide a combination of automatic and manual responses, along with notifications to customers if they would like to receive these - giving you total control.